The Top 4 DDoS Attack Vectors Threatening 5G Networks
Distributed Denial of Service (DDoS) attacks have plagued commercial and enterprise networks since the seventies. In terms of damage to network infrastructure, service continuity and business reputation, DDoS attacks account for some of the most successful cyberattacks in history.
In the past, Communication Service Providers (CSPs) assigned low risk to their chances of being attacked and avoided taking protective measures, assuming they could dodge the DDoS bullet.
However, the prevalence of IoT devices have made it easier to launch flooding attacks and to increase the scope of damage. “Bad actors” are using multitudes of connected devices to overwhelm target network nodes or communication links with fake traffic. In addition, CSPs often suffer “collateral damage” from attacks that flood their networks on the way to the actual, designated target.
With 5G, vulnerability to DDoS attacks has dramatically increased
In order to achieve lower latency, which is critical for many new applications, such as Vehicle2Vehicle communication, 5G has a distributed network architecture with Multi-access Edge Computing (MEC) at multiple remote locations. These additional points of access, combined with a growing densification of connected devices, and the proliferation of open-source applications, increase the “attack surface” and create additional vulnerabilities.
Furthermore, higher wireless speeds dramatically increase the impact of DDoS attacks over the network as each device can generate an order of magnitude higher attack throughput to the network (at MECs and at the core). As mentioned, this effect is amplified by the plurality of IoT devices, which is expected in 5G, as IoT devices tend to be more vulnerable to cyberattacks.
What is a DDoS attack?
Typically, the objective of these DDoS attacks is to make network services unavailable. DDoS can also be used as a smokescreen for other malicious activities, such as infiltrating malware and ransom attacks or exfiltrating sensitive data. To make matters more complicated, DDoS can come as repeated bursts of several tens of seconds, or as a constant high load of terabits per second.
CSPs can no longer afford to take a reactive approach that assumes, ”If it hasn’t happened to my network, it probably won’t. And if it does, I’ll handle it then.” Deferred action is no longer a viable option.
One of the main factors driving CSPs to adopt a DDoS protection strategy is the rise in enterprises who are migrating data centers and IT infrastructure to the service provider cloud. Business services are a growing source of CSP revenue. They are based on SLAs defining service capacity, availability and performance that the CSP promises to deliver. To meet SLAs, this business needs to be protected from attack.
Another factor is the Quality of Experience (QoE) that consumers expect from their CSP. Sluggish response time is not appreciated, and downtime is not tolerated. If not properly mitigated, DDoS attacks can have a dramatic impact on QoE for users. Furthermore, there can be serious financial impact and reputation damage – even block-listing by other operators.
To assure service availability and performance, CSPs must take measures to protect against DDoS attacks designed to overwhelm network resources and deny service to legitimate users. Nowadays, leading CSPs are doing something about it and are prepared to detect and mitigate various types of DDoS attacks.
The Top DDoS Attack Vectors Threatening 5G Networks
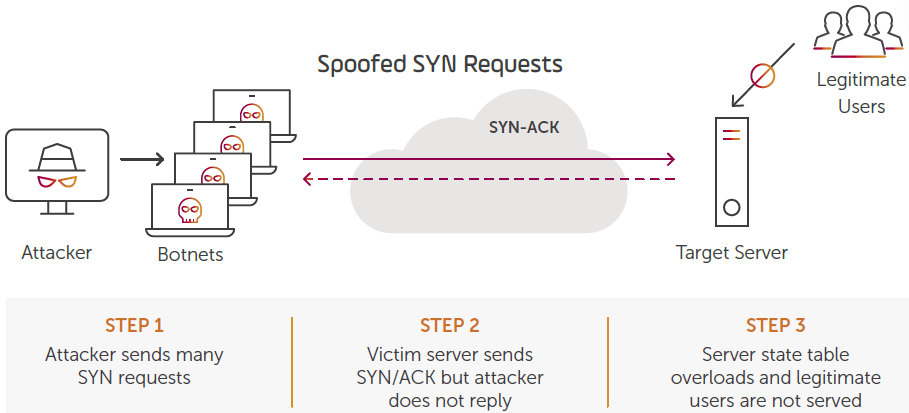
1. SYN FLOOD
A SYN Flood, often generated by botnets, is designed to consume resources of the victim server, such as firewall or other perimeter defense elements, in an attempt to overwhelm its capacity limits and bring it down. The target receives SYN packets at very high rates which rapidly fill up its connection state table, resulting in disconnections, dropping of legitimate traffic packets, or even worse – element reboot.
An example of a SYN FLOOD DDoS attack.
SYN Floods exploit the TCP (Transmission Control Protocol) three-way handshake process to wreak havoc. The attack floods multiple TCP ports on the target system with SYN messages requesting to initiate a connection between the source system and the target system. The target responds with a SYN-ACK message for each SYN message it receives and temporarily opens a communications port for the requested connection while it waits for a final ACK message from the source in response to each SYN-ACK message. The attacker never sends the final ACK and therefore the connection is never completed. The temporary connection will eventually time out and be closed, but not before the target system is overwhelmed with incomplete connections accumulated in its state table.
2. UDP FLOOD
In a UDP Flood, attackers send small spoofed UDP packets at a high rate to random ports on the victim’s system using a large range of source IPs. This consumes essential network element resources on the victim’s network which are overwhelmed by the large number of incoming UDP packets. Often victim servers start to reply back with ICMP destination unreachable packets.
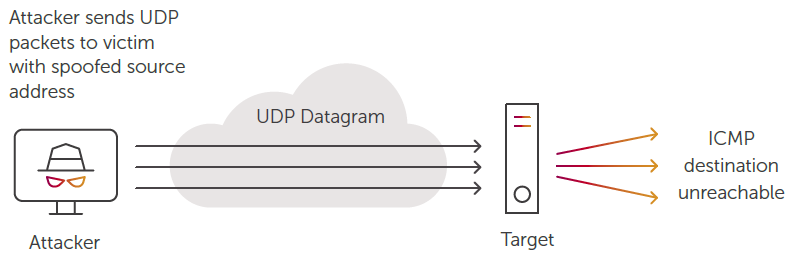
UDP attacks are difficult to detect and block because they often do not match a consistent pattern and are therefore effective in exhausting network resources until they go offline.
3. UDP FRAGMENTATION
UDP Fragmentation attacks send large UDP packets (1500+ bytes) which consume more network bandwidth.
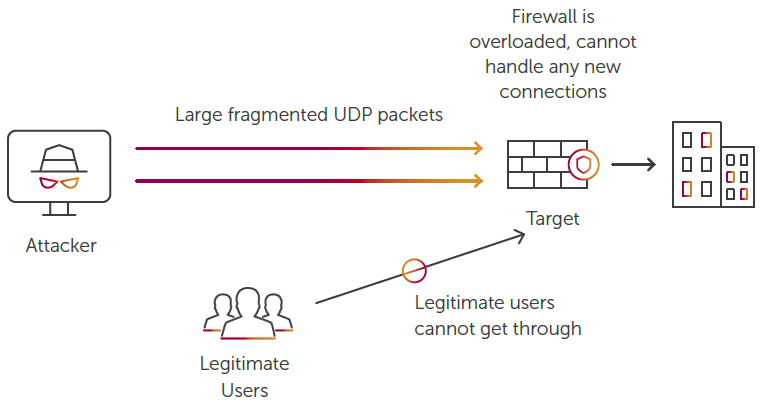
Since the fragmented packets usually cannot be reassembled, they consume significant resources on stateful devices such as firewalls along the traffic path. When combined with other types of flood attacks, this may result in drop of legitimate traffic by the destination server being flooded.
4. DNS FLOOD
A DNS Flood sends spoofed DNS requests at a high packet rate and from a wide range of source IP addresses to the target network. Since the requests appear to be valid, the victim’s DNS servers respond to all the spoofed requests, and their capacity can be overwhelmed by the sheer number of requests.
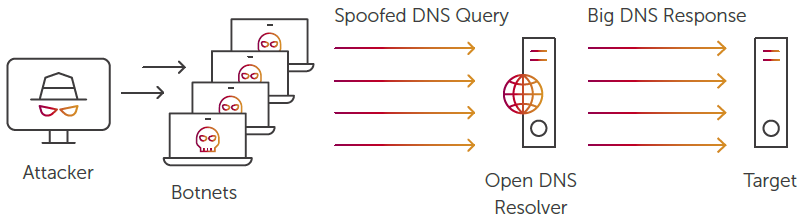
This attack consumes large amounts of bandwidth and other network resources. Eventually, it exhausts the DNS infrastructure until it goes down, taking the victim’s Internet access (WWW) and offline hosted sites with it.
When it comes to DDoS, now is the time to act
DDoS attacks are here to stay. They keep getting bigger, more frequent, and increasingly sophisticated. Current strategies can’t keep up. With 5G, virtually everyone is vulnerable, and things are only going to get worse.
To learn more and get info about other types of DDoS attacks beyond the four types mentioned above, check out the Glossary of Common DDoS Attacks. You can also read more about Allot’s DDoS Secure product offering and DDoS Protection solution for service providers.