
From the Flu to DDoS – an Epidemic of Epidemics!
Last week, while the mobile industry was busy celebrating telecom innovation at MWC, another innovation was making headlines: a record 1.35 Tbps DDoS attack was launched (and it has already been surpassed), causing some disruption and highlighting the potential for much worse. In this instance, the attack was detected and mitigated relatively quickly—but it required manual intervention and rerouting of traffic. DDoS is an epidemic of the connected world and like the flu, it is a worldwide problem, it can be quite harmful if not treated on time and it seems to be getting worse.
It is no secret that this has been an especially rough flu season. In January, Time magazine explained the phenomenon:
“The flu shot is tweaked each year in an attempt to target what are projected to be the most prevalent strains of the disease, but the process isn’t foolproof.”
And therein lies the rub. The vaccine is a static defense that targets specific, projected flu strains, and in reality, is effective against only 30% of H3 viruses. Telecom operators face the same problem with traditional DDoS mitigation solutions. They only know how to mitigate what they already know (“known knowns”). The challenge for ISPs and enterprises is the same as that facing health professionals—how can you defend against the non-prevalent strains—the unforeseen DDoS attacks, the new vectors, the zero-day exploits (“unknown unknowns”)? Fortunately, the world of data communications has a solution that is not yet available in medical practice. Autonomously adaptive, machine-learning algorithms utilizing artificial intelligence techniques to automatically detect anomalous behavior and trigger mitigation of, as yet, unknown attack profiles. In the latest attack on GitHub, IT professionals noticed an unusual spike in inbound traffic caused by the amplification of UDP traffic reflection through memcached servers’ default port 11211. They rerouted traffic to a scrubbing center provider that cleaned out the malicious packets and the attack ended shortly afterward. 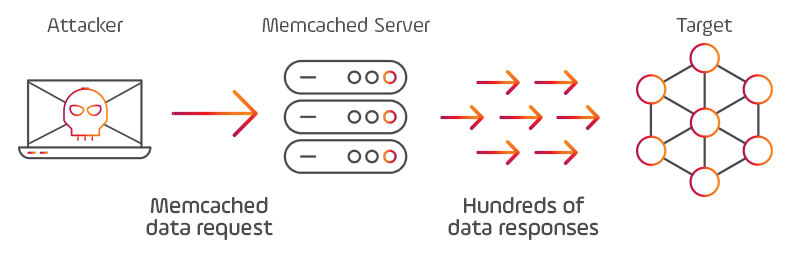 Fortunately, service was only disrupted for a few minutes, but it could have been much worse and other targets might not have been as ready. Companies on the scale of GitHub can divert terabits of traffic to external DDoS cleanup services, but for many service providers (and enterprises) the cost in scrubbing and latency are prohibitive. As 5G and IoT expand the scale of data communications, this problem will become even more acute. In addition, many short-term “hit and run” attacks evade external detection due to their short time stamp and will not get scrubbed. But there is a better solution. Imagine if your network had a high-performance, distributed inline system that used machine learning techniques to automatically detect and mitigate any type of attack at wire speed, regardless of scale, within seconds and without disrupting service. Legitimate traffic would be unimpeded, while malicious traffic would be discarded. No manual intervention would be required.
Fortunately, service was only disrupted for a few minutes, but it could have been much worse and other targets might not have been as ready. Companies on the scale of GitHub can divert terabits of traffic to external DDoS cleanup services, but for many service providers (and enterprises) the cost in scrubbing and latency are prohibitive. As 5G and IoT expand the scale of data communications, this problem will become even more acute. In addition, many short-term “hit and run” attacks evade external detection due to their short time stamp and will not get scrubbed. But there is a better solution. Imagine if your network had a high-performance, distributed inline system that used machine learning techniques to automatically detect and mitigate any type of attack at wire speed, regardless of scale, within seconds and without disrupting service. Legitimate traffic would be unimpeded, while malicious traffic would be discarded. No manual intervention would be required.
How does DDoS protection work?
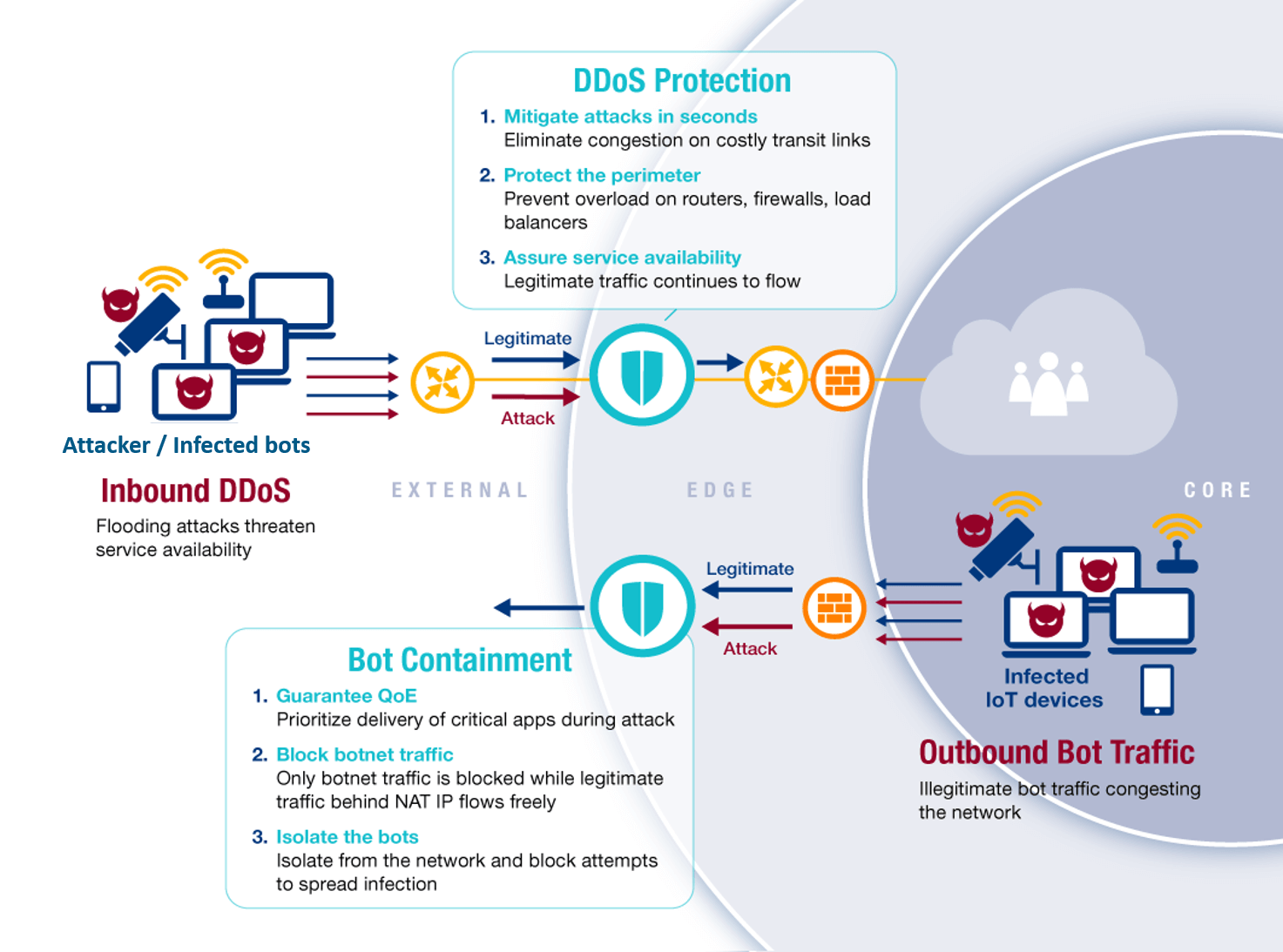 In the above architecture, every packet of data is inspected by high-performance, distributed inline appliance instances. Attacks are automatically detected and surgically blocked within seconds before they threaten or disrupt network services. Using advanced Network Behavior Anomaly Detection (NBAD) technology, volumetric attacks are detected by the anomalies they cause in the normally time-invariant behavior of Layer 3 and Layer 4 packet rate statistics. The dynamic creation of mitigation rules and surgical filtering of attack packets prevents over-blocking and enables legitimate traffic to flow unimpeded, assuring network protection and service QoE at all times.
In the above architecture, every packet of data is inspected by high-performance, distributed inline appliance instances. Attacks are automatically detected and surgically blocked within seconds before they threaten or disrupt network services. Using advanced Network Behavior Anomaly Detection (NBAD) technology, volumetric attacks are detected by the anomalies they cause in the normally time-invariant behavior of Layer 3 and Layer 4 packet rate statistics. The dynamic creation of mitigation rules and surgical filtering of attack packets prevents over-blocking and enables legitimate traffic to flow unimpeded, assuring network protection and service QoE at all times.
There is an additional, often overlooked aspect to DDoS attacks that service providers should consider. Service providers themselves can be infected and become the source for outgoing botnet attacks, harming their customers and their reputation. Outbound attacks can only be caught by inline systems that inspect all packets, traveling in every direction. In addition to blocking such attacks, inspecting outbound traffic also enables better detection of inbound attacks. By correlating bi-directional traffic, the system can easily highlight inbound traffic that is masquerading as responses to requests that were in fact not sent from the service provider.
During the recent memcached attacks, Allot’s bi-directional, inline DDoS Secure solution successfully detected and prevented such attacks observed in multiple customer networks worldwide. Below is an example:  So, while this year’s flu season may be winding down, DDoS is just gearing up. New vectors, new vulnerabilities and ever growing volumetric attacks are just a matter of time. Get protected – inline and on time!
So, while this year’s flu season may be winding down, DDoS is just gearing up. New vectors, new vulnerabilities and ever growing volumetric attacks are just a matter of time. Get protected – inline and on time!



